
Technologies for Optimized Remote Access
- IPsec VPN
The latest protocol standard for the set-up of IP-VPN's. - SSL VPN
This remote access technology is perfectly suited for web applications, sporadic users as well as business partners and customers. - Friendly Net Detection
Friendly Net Detection (FND) is a technology that allows to automatically recognize "friendly networks". - VPN Path Finder
Highly secure mobile computing - even in IPsec-hostile remote access environments. - Seamless Roaming
VPN tunnel without interrupting mobile computing sessions. - Network Access Control
Optimized network access control for remote access environments. - High Availability Services
Optimized network access control for remote access environments. - Overlapping Networks
Even within overlapping networks, our remote access technology ensures trouble-free connection set-ups.
IPsec:
The Preferred VPN Technology
The Internet Engineering Task Force's (IETF) IPsec-specification is the latest protocol standard for the set-up of IP-VPN's. It is known to be technically mature and provides a perfected method for external business communication in unprotected public networks. Additionally, the future IPv6 contains IPsec as its basic technology.
All VPN solutions, which are currently available, contain IPsec functionalities. However, there are differences in IPsec solutions. The decisive factor for the quality of a solution is, which kinds of IPsec protocols the supplier supports. By only implementing proprietary protocol expansions of the IPsec protocol for remote access, the user is led nowhere. As early as 2002, NCP developed an IPsec protocol-stack, which matches all the IETF objectives and supports all IPsec standards according to RFC.
Security solutions, based on IPsec VPN technology, have to support all peripheral and central components as well as systems in all remote access environments - this is the standard the user can expect, hence, this is the standard a solution has to meet. In order to meet these standards and in order to optimize for remote access, NCP has expanded the IPsec-stack by special protocols (e.g. XAUTH, IKE-Config-Mode, NAT Traversal (NAT-T), Dead Peer Detection (DPD)).
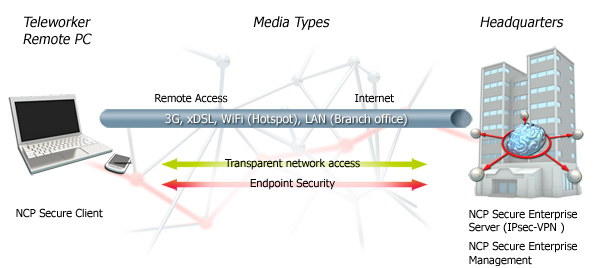
NCP's Next Generation Network Access Technology allows for highly secure IPsec VPN connections behind firewalls, whose settings are designed to prevent IPsec based data communication (e.g. in a hotel). The technology behind this feature is called NCP's VPN Path Finder Technology.
Strong authentication via one-time password token (OTP), certificates or biometric data via PKCS#11 is a further security feature of NCP's Secure Communications Solution. The solution supports both, user and / or hardware certificates. Click here for further information.
SSL VPN:
The alternative Remote Access technology to IPsec
SSL is the acronym for Secure Socket Layer. SSL is the acronym for Secure Socket Layer. Originally, this technology has been developed in order to allow encrypted communication between web browser and web server. SSL VPN is usually referred to in combination with remote access. The fundamental idea behind SSL VPN approaches was to simplify the remote access to Intranet environments and to avoid the need of installation of a VPN client at the end device. This, however, is not sufficient anymore since modern remote access to a company network is subject to various, individual requirements.
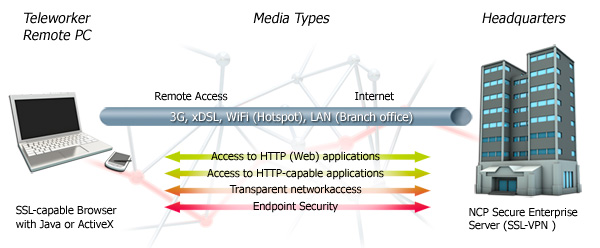
Overview of functionalities of the NCP Secure Enterprise SSL VPN Server
For this reason NCP offers three different access methods:
- If you wish to exclusively access your company’s network web applications and data server through a web browser, it is best to use a browser based SSL VPN (Web Proxy). This method puts the fundamental idea behind SSL VPNs into practice - it eliminates the need to install additional software at the end device. NCP's Secure Enterprise VPN Server (SSL) isolates the internal web server from direct access from the Internet. Only after successful authentication at the SSL VPN gateway, the user is granted access to the gateway.
- If you wish to access non-http-enabled applications and to use a SSL VPN tunnel to communicate with your company server within the company network, it is best to use a "Thin Client" SSL VPN. The thin client has to be installed at the end device and can be downloaded via a web browser. It uses NCP's Port Forwarding Technology to open ports, configured by the administrator. These local ports allow software to securely communicate with the designated server within the company network.
- If the goal is to have fully transparent network access to the central network, it is best to use NCP's PortableLAN Client. Similar to IPsec, it is mandatory that this VPN client software is installed on the end device. This client is the virtual connection which transmits the whole network traffic via the encrypted SSL connection, which in turn connects the remote computer to the company network.
NCP's Secure Enterprise VPN Server (SSL) offers connectivity, comprehensive security through endpoint security and individual access control. It supports strong authentication features such as one-time-password-tokens (OTP), text messages (text/SMS) or digital certificates. The software can be scaled according to actual needs and it can either be installed directly on the hardware, using the operating systems Linux or Windows, or as virtual machine.
Additional information:
Friendly Net Detection:
Part of NCP's Security Management
Friendly Net Detection (FND) is a technology that allows the computer to automatically recognize "friendly networks", FN in short. It is our aim to guarantee maximum security for the central data network in remote access VPNs (Virtual Private Networks) and to provide the user with secure and transparent access to the company network - no matter in which network environment the user is working.
FND is a classic client / server application. The FND server (FNDS) is a separate service which is installed independent of the VPN gateway. It can be installed on any computer within the "known company network". The FND client (FNDC) is part of NCP's Secure Client Suite. It is configured within the clients firewall settings.
The FND technology is based on established standards and guarantees consistent system security. Furthermore, it protects your system from errors which are frequent in proprietary solutions.
Prerequisite for the use of FND is installation of FNDS in a network that has been declared as FN. This service has to be available from all ports of the network; i.e. in some cases, router settings may have to be changed.
If an employee connects his end-device to the company network, the FNDC tries to contact the configured FNDS. If the device is able to contact and authenticate with the FNDS, it is confirmed that the device is within a FN. The firewall rules of the NCP Secure Client are automatically set on "internal operation".
The administrator centrally sets all rules of the personal firewall, which comes as standard with the NCP Secure Client. The user can neither manipulate nor deactivate these rules.
In large remote access VPN's, all templates and changes of all configuration parameter of the NCP Secure Client are ideally carried out with NCP's Secure Enterprise Management (SEM) System as "Single Point of Administration".
VPN Path Finder Technology:
Highly secure mobile computing - even in IPsec-hostile remote access environments
The patented VPN Path Finder technology is a new remote access technology, developed by NCP. It removes a major constraint in communication within IPsec VPNs by allowing data connections from unknown networks, whose firewall settings deny IPsec communication and only allow internet access to web browsers.
With the help of NCP's VPN Path Finder Technology, NCP's Secure Client automatically recognizes when the company's VPN gateway is not available via IPsec. When this is the case, the client software automatically switches to a modified mode ("emulates" HTTPS) and sets up an end-to-site tunnel to the company network.
With this technology, highly secure VPN connections based on IPsec are possible even on hotel and public hotspot networks with restricted security access settings or in certain mobile communication networks.
The advantage of this solution is that the administrator maintains the corporate security policy based on IPsec. The user benefits from having a working connection in every environment.
How it works:
A prerequisite for the VPN Path Finder technology is an NCP Secure Enterprise VPN Server. An alternative port has to be configured in the VPN gateway settings. The VPN Path Finder technology automatically switches to the alternative connection protocol TCP encapsulation of IPsec with SSL header (via port 443) if the device cannot establish a standard IPsec connection via port 500 or UDP encapsulation. If you set up a connection via port 443 with the VPN Path Finder technology, the graphical interface displays an icon. It also appears in the interface of the Windows logon via the NCP credential provider.
If a proxy server is required, you can configure it by selecting "Proxy for VPN Path Finder".
Seamless Roaming:
Always online: "Seamless" Roaming in a Remote Access VPN Environment
There are three ways for mobile devices to set up a secure VPN tunnel (Virtual Private Network) to the company network: the traditional wire-bound Ethernet LAN, Wireless LAN (WiFi) at public hotspots, hotels or companies as well as cellular network connections. For cellular network connections the system has to support the following three technologies: the GSM network, 3G connections and high-speed connections via 4G networks (LTE, Long Term Evolution).
With "Seamless Roaming" the devices are able to automatically change between various networks. Increasing mobility and employees who roam freely within a building or company premises will profit from seamless roaming and a permanent availability of applications. This flexibility, however, poses a challenge to a remote access VPN solution. They have to
- automatically support any change of communication medium
- dynamically redirect an existing VPN tunnel during a change of the medium and
- prevent session loss.
NCP's IPsec VPN Client software is one of the first client software's worldwide that supports seamless roaming of VPN connections across various mediums - without compromises regarding security. Seamless roaming is only available in conjunction with NCP Secure Enterprise VPN Server The client is able to automatically change the communication medium during a session and to dynamically redirect the VPN tunnel. Combined with this, the client also ensures "Location Awareness", which means automatic recognition of secure and insecure networks. The feature "Friendly Net Detection" ensures that the system activates or deactivates the appropriate firewall policy without the user's help.
Furthermore, the VPN client ensures that the VPN tunnel remains in place even if the connection has been interrupted; for example when the cellular network has been disconnected during a train journey. In such a case, the logical connection remains in place even if the VPN client has no access to the VPN server. The client software informs the user of the temporary disconnection of the physical connection by setting the state of the VPN tunnel, displayed by the monitor, from green to yellow.
During seamless roaming operation, the software automatically controls DPD handling so that neither gateway nor client terminate the VPN connection during an interruption of a physical connection. DPD (Dead Peer Detection) is a process that recognizes if a VPN connection on the basis of IPsec has been interrupted and allows fresh set up of the tunnel.
For VPN access via a cellular network, as with the example of the train journey, it is important that the VPN solution automatically re-establishes the connection as soon as the network is available. This process is transparent to the user so that no operation error occurs and that he is relieved from this task.
Operating comfort is further increased since the user of the VPN client does not have to worry about which medium is "best" - WiFi or cellular network. Ideally the user only has to click the connect button and the client software selects the appropriate available communication medium which the network manager specified under policies.
Network Access Control:
Network Access Control during access to your corporate network
In a Virtual Private Network (VPN), each end device is a potential gateway to the central network. A personal firewall does not offer sufficient protection against hacking. In order to protect your business against industrial spying and economic crime, you have to employ various different security mechanisms which are centrally supervised and coordinated.
From the legal perspective, too, access control has become essential in order to provide secure operation or corporate networks.
The market offers various Network Access Control (or Network Admission Control) Solutions (NAC) most of which are complex and difficult to manage. Of course, NAC is part of NCP's holistic VPN solution and it is optimized for all remote access demands.
It is obligatory for each accessing device to verify itself to NCP's central Secure Enterprise Management. Usually, the software verifies a number of information of the client platform. The purpose of NAC is to only allow network access to devices which have been classified as safe during examination.
Use the NCP Secure Enterprise Management in order to create NAC security policies and assign them globally, group-specifically or individually to the clients. The security policies define whether a device meets the preset requirements and whether it is allowed network access.
NCP's Network Access Control (NAC) comprises several steps:
- Identification of the devices
- Checking compliance with the corporate security policy
- Depending on the result, the end device is allowed network access or put into quarantine
- After compliance to the security policies is restored, the end device is allowed access to applications and the corporate network.
- If the end device does not comply, it is disconnected
The NAC software operates in real time and recognizes all accessing clients. Without real time control, hackers have a host of opportunities to attack a network and to import malware. For this reason NCP's NAC solution excludes conspicuous or unknown devices from the network and puts them in quarantine.
A device in quarantine has to pass several security checks, which have been defined by the administrator previously. NCP's NAC software analyzes if, for example, current service packs, patches or up-to-date antivirus engines have been installed. Furthermore it examines services and file information as well as registry values. Based on filter rules at the VPN gateway and in the NCP Secure Enterprise Management, the NAC software constitutes an essential buffer zone ahead of the network.
This means, meeting corporate security policies is mandatory for each device while the user can neither avoid nor manipulate them.
Overview of all functions of NCP's NAC solution:
Identification
Clear identification and localization of Remote Access clients in the network.
Authentication
Clear authentication of the user’s identity and / or terminals using e.g. active directory and RADIUS server (EAP).
Endpoint Policy Enforcement
This checks if remote access clients comply with the company’s security policy if e.g. the operating system is admissible, required patches are installed or the most recent antivirus engines are installed or if the most recent signature is available.
Remediation
This function puts a client which does not comply with the security policy into the quarantine zone. A range of options apply in quarantine that allow the user to work in a constricted fashion or to establish client conformity by providing relevant information.
Differences to the target specification are logged and can trigger the following notifications or actions, for example:
- Notification display at client
- Notification output in the client log
- Sending of a notification to the management server
- Sending of a notification to a Syslog server
- Activating firewall rules
- Stopping the VPN connection
Continuous check
The check is not only carried out for the first attempt of connection establishment to the network but for each connection establishment after that. It is, furthermore, repeated in a pattern which is established in the policy.
Cost-efficient
Fast and cost-efficient implementation and administration is guaranteed as part of the integrated NCP Remote Access solution. This also means low operating costs and a fast return on investment (ROI).
Compliance requirements
NCP’s NAC solution records all security relevant information transparently and makes them available in a clear form.
High scalability
The modular software architecture of all NCP VPN components allows a tailored expansion with state-of-the-art products with inexpensive updates/upgrades.
The solution for Windows 32/64 bit operating system is currently available. PDAs, smartphones etc will be supported in the near future.
The following questions should be clarified prior to implementing a NAC solution:
- Who may login into the network?
- Which VPN technology shall be used where?
- To which extent may the network be accessed?
- Can resources potentially be grouped?
- Were all required resources identified for the relevant groups?
- Which functional range is desired for which area?
- What are the local restrictions? (physical / logical)
- May existing data be used for authentication / authorization?
High Availability Server:
Your insurance against deficiencies and failures
Access to central databases and resources has to be guaranteed "24/7/365". Only a faultless operation of a VPN system guarantees success in the planned corporate and economic use of the undertaken investment.
The "NCP Secure Enterprise High Availability (HA) Services” guarantee the highest level of availability or failsafe protection of central systems regardless if one or several NCP Secure Enterprise VPN Servers are installed. All VPN tunnels are available at all times.
We distinguish between two scenarios depending on the number of installed NCP Secure Enterprise VPN Servers:
- One NCP Secure Enterprise VPN Server, it concerns backup functionalities; NCP Secure Enterprise Failsafe Server is used for this scenario. In case of a failure it is switched to a Secure Enterprise Server Backup System.
- Several parallel NCP Secure Enterprise VPN Servers i.e. it concerns also an even system utilisation in addition to backup functionalities; NCP Secure Enterprise Load Balancing offers the required performance in this environment. The faulty VPN gateway is automatically taken out of the productive operation in case of a malfunction event. The VPN tunnels are distributed onto the VPN gateways still available.
Both high availability servers are also configured redundantly due to availability reasons.
Changes to configuration, updates and upgrades are carried out easily via the Windows interface of the high availability manager which can be installed on any console processor in LAN.
Supported operating systems:
- Windows Server 2003 R2 Enterprise Edition (32/64 Bit) / 2008 Enterprise (32/64 Bit) / 2008 R2 Enterprise (64 Bit) / 2012 Datacenter (64 Bit) / 2012 R2 Datacenter (64 Bit)
- Linux: Kernel Version 2.4.10
Download the NCP Secure Enterprise High Availability Services (PDF).
Overlapping Networks:
Problems with overlapping networks?
Have you experienced difficulties during logging in into the corporate network with your current VPN solution? Has your log in effort proved futile, although connection setup seemed to be successful? Such problems are often caused by overlapping networks.
An overlapping network (subnet) is when you establish a connection from the VPN client to another network with the same ‘private IP address range’, and an ‘overlap’ occurs with the addresses. I.e. the hotel router assigns your machine a ‘private IP address range’, i.e. 192.168.1.0, and this address matches the office’s. When the client connects, it uses the source IP address it currently has, which is the home network. The gateway sees this as an internal (local) address, and thus networks overlap and deny your VPN connection.
The technology behind NCP's Enterprise Solution prevents problems with "overlapping networks".
