
Everything a Remote Access VPN needs
Virtual Private Network (VPN): Essential for modern Remote Access
A remote access VPN solution is only as good as the sum of its components' (client and server) features. This, however, does not only include a simple evaluation of technical aspects.
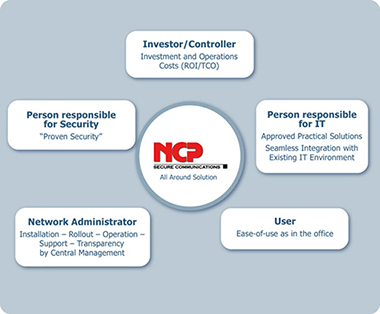
A top notch remote access VPN has to meet the requirements of everybody involved in the decision process - users, administrators, security administrators, investors and controllers. Basically it is about:
- Usability
- Security
- Economic Efficiency and Universality
The system has to meet the requirements of everybody involved in the decision process.
A Remote Access VPN requires Usability:
As easy as could be
End devices that are easy and intelligible to operate are every user's dream. Administrators, however, demand the same level of transparency and manageability in the wide area network (WAN) as they are used to from the local area network (LAN).
In order to meet the wishes of all users, NCP's remote access VPN solution offers comprehensive automatisms as well as configuration, display and surveillance options.
NCP Remote Access VPN – overview of the most important features:
- Intuitive graphical user interface
- Integrated support for 3/4G cards
- Easy setup and management of a client configuration
- Mobile broadband support
- Automatic media recognition
- APN from SIM Card
- Wi-Fi roaming
- Seamless Roaming
- VPN Path Finder
- IKEv2 support
- Fully automatic operation of a VPN by central management
- Comfortable domain registration
- Automatic, location-aware adaption of firewall rules
Intuitive graphical user interface
Independent of the operating system, all NCP VPN Clients graphically display all connections and security statistics. Comprehensive cursor-sensitive tool tips offer quick information in clear text. Designed as one click solution, the software automatically carries out connection setup to the company network, while the user is able to monitor all phases. If an error occurs, it is displayed in red. It simplifies troubleshooting and support.The summary language selection facilitates international application.
Integrated support for 3/4 G Cards
NCP's Secure Client integrates and supports 3/4G cards of various suppliers, i.e. displays them in the Client Monitor. This integration and support is the key to the display of field strength, provider and selected radio network. The installation of delivered management software of maps distributors and the associated call for an additional user interface can be cancelled.
Easy setup and management of a client configuration
Each NCP Secure Client has its own configuration file in which it saves all connection parameter. The administrator can specify each parameter field and may store these as necessary against additional changes by the user. That creates configuration freedom for the realization of individual remote-access requirements.
Mobile broadband support for Windows 7
LTE currently allows the highest wireless communication rates. Since the virtual COM ports used before Windows 7 had become a bottle neck with LTE data communication, using Windows Mobile Broadband Interface now ensures maximal data communication speed. A further advantage of Mobile Broadband Support is the integrated dialer of NCP's VPN Client which automatically supports all current and future 3G/4G cards of Windows 7.
APN from SIM Card
The APN (Access Point Name) defines the access point of a mobile data connection at a provider. If the user changes provider, the system automatically takes APN data from the corresponding SIM card and uses it in client configuration. Through that, it is easy to use inexpensive, local providers abroad.
Automatic Media Recognition
The NCP VPN Client checks each connection establishment that selects available transmission media and automatically chooses one from the given sequence. The manual network selection is naturally given further on.
Wi-Fi roaming
If a teleworker moves within the reception area of several access points using the same SSID, the system automatically chooses the strongest access point available. Applications which communicate via a tunnel do not even "notice" this access point roaming.
NCP's Secure Client is able to roam access points within a company network (e.g. while changing locations with a laptop) without having to set up a new data connection and logon to the gateway, again and again. This allows for continuous remote access despite changing IP addresses.
Seamless Roaming
You can call "seamless roaming" the logical advancement from "WiFi roaming". With "Seamless Roaming" the devices are able to automatically change between various networks, for example between LAN, WiFi and 3/4G. This further facilitates mobile computing and enables the state "always on" - meaning continuous and constant availability of applications of the mobile telework station. The client is able to automatically change the communication medium during a session and to dynamically redirect the VPN tunnel, while the user does not even notice this process.
VPN Path Finder
This feature allows for remote access behind firewalls whose settings prevent IPsec based data traffic (Port 500 or UDP encapsulation not possible). With the help of the VPN Path Finder technology, the NCP Secure Client can use Port 443 of the firewall (Fallback IPsec / HTTPS). This allows for a holistic IPsec-based implementation of the security policy (prerequisite: NCP VPN gateway, starting with v 8.0, at the corporate headquarters).
IKEv2 support
In contrast to IKEv1, IKEv2 is faster during connection set up because it needs fewer prompts than its predecessor. Apart from that IKEv2 supports various protocols (e.g. NAT-T, DPD) which were required but not supported by version 1. Instead of XAUTH, EAP is used as the basis for authentication. The Mobility and Multihoming Protocol (MOBIKE) ensures higher reliability of IPsec tunnels in mobile applications. NCPs VPN Client Suite is designed to be easy to configure and allows performant connection setup. The specifications of IKEv2 make setup of virtual private networks easier, more flexible and more reliable. Supporting IKEv2 makes the NCP VPN Client Suite compatible to almost every other available VPN gateway - amongst others the Microsoft Windows Server 2008 R2.
Fully automatic operation of a VPN by central management
You can also integrate NCP's Secure Enterprise Clients into a centrally managed, cross-company VPN. This includes tasks like client configuration, mass rollouts, software updates, certificate administration and checking security policies. NCP's Secure Enterprise Management (link) manages these tasks.
Comfortable domain registration
The users can register comfortably without intricate changes between various user interfaces onto Windows domains – this also applies to UMTS and GPRS. A transmission medium is already selected during the booting phase. After automatic media selection and entry of a PIN (for SIM or certificate), a tunneled connection is created to the company network, where domain registration – likewise automated – can take place.
All NCP Secure Clients have a dynamic personal firewall.
Check it out on NCP Dynamic Personal Firewall
A Remote Access VPN requires Security:
Secure VPN without compromises
A remote access VPN has to guarantee confidentiality, integrity and availability of information and systems. NCP's remote access VPN solution guarantees this security. It sustainably protects your end devices and communication mediums from attacks by using seamlessly interacting security mechanisms. Security levels are not static but constantly changing. To meet those changing but current threats in time, all security features have to be upgraded to cutting edge technology. NCP's software components are inexpensive due to low cost updates or upgrades.
Availability of data and systems is a further security issue in a professional VPN. The task is to avoid errors with communication mediums and to prevent downtimes of central systems.
NCP Remote Access VPN – overview of the most important security features:
- Dynamic personal firewall with "Friendly Net Detection"
- VPN tunneling on the basis of IPsec and SSL
- Encryption
- Strong authentication
- Endpoint Security – Quarantine Zone
- Parameter lock
- Line Backup
- System Availability (HA-Services)
- Protection of data on the terminal equipment – cache protection (SSL VPN)
- Enforced internet connection over company headquarters
- FIPS Inside
Dynamic Personal Firewall with Friendly Net Detection (location awareness) - optimized for remote access
This personal firewall serves to protect terminal equipment against internet attacks, WiFi and LAN. It is a component of all NCP Secure Clients, therefore independent of the operating system and may be centrally administered (Enterprise Solution). PC protection takes place during system startup and automatically conforms to the prevailing remote access environment. "Friendly Net Detection" provides automatic recognition of secure and insecure networks. This means the system activates or deactivates the appropriate firewall policy without the help of the teleworker. The administrator centrally sets parameter locks, which provide further security. They prevent users from manipulating or accidentally deactivating the configuration. With this feature, even security sensitive locations like public hotspots can serve as access points to the company network.
The personal firewall remains active as desired if the VPN service is deactivated.
An overview of the functional environment of the NCP Personal Firewall:
- IP-Network Address Translation (IP-NAT)
- Stateful Packet Inspection
- Applications-independent filter rules
- Protocol, port and address-based filter rules
- Friendly net recognition
- Automatic hotspot recognition
- Connection-dependent filter rules
- Voluminous logging options
Secure VPN: VPN tunneling on the basis of IPsec and SSL
NCP's Secure Enterprise VPN Server reliably supports both VPN technologies. No matter the technology - IPsec VPN client, SSL clientless, SSL thin client, SSL fat client - remote access to the central data network is secured at all times, demand-oriented.
Encryption
NCP's VPN solution always supports the markets latest, high performance algorithms and key lengths. Fast and inexpensive, you can download software updates from the Internet.
Strong authentication
In a VPN, it is no longer sufficient today to allow access to the company network through user-name and password. Both are easy for hackers to spy out. For this reason, NCP only uses strong authentication methods for its VPNsolutions. The methods are: OTP token (one time password), digital certificates within a PKI (public key infrastructure) and biometric technologies. The one-time passwords are generated dynamically, replacing the static passwords and immediately lose their validity after use. Digital certificates dispose over a still higher degree of protection and are universally applicable as well. You can apply it as software or on a Smart Card as an X.509 v3 certificate. When required, it can be collaborated with several trust centers/certification (CA's) (multi CA-support).
Endpoint Security (NAC) - Quarantine Zone
Endpoint security - also known as Network Access Control or Network Admission Control (NAC) - means that NCP's Secure Enterprise Clients check all security relevant parameters prior to the device's access to the company network. In this way, it can handle such items as the status of the virus scanner, server information, certificate content or software status. Adherence to security directives is compulsory and may not be manipulated by the user.If a device does not comply with the policies, it is led into a designated quarantine zone within an VPN. The following options are available:
- All security directives fulfilled:
- Access to the productive network
- If only one of the security parameters is not fulfilled, then the following can be defined:
- Final destination in the quarantine zone with limited server access for software update of the remote system
- Start external applications on the remote PC
- Disconnection
Parameter Lock
The parameter locks have two main functions: The first is to reduce the complexity of configuration possibilities. This function hides parameter folders for features which are not used, so that the user only sees the settings which are relevant for his working environment. The second function is that pre-settings can be made which the user cannot change. This avoids misconfigurations and undesired connection set ups.
Line Backup
The line backup secures high accessibility for the target system, even during a disturbance of the transmission path (DSL connection). Disturbances or bottlenecks in the internet can never be ruled out. Connection breaks often lead to data loss and longer queue times until the error is fixed. Both are unpleasant for the VPN carrier and associated with unanticipated higher costs (e.g. important data are untimely available. With the "line backup" feature, a disturbance is automatically switched over by a DSL or ISDN connection on an ISDN backup line (network administration is informed). The data connection persists, i.e. it can continue to work without new reporting (no session loss). After secondarily produced DSL functionality, it is automatically switched back to the higher value connection.
System Availability
The high-availability services of the Secure Enterprise Solution provides for the higher degree of availability of the Secure Enterprise VPN Server with their backup and load-balancing mechanisms. These services ensure that at any point in time – also in the event of a disturbance – all VPN tunnels are available to access the company network. Additional information may be found here.
Data protection on the terminal equipment – cache protection (SSL VPN)
In order to sustainably counter attacks from the internet, it can be centrally specified that the selection over a VPN tunnel to the company network and its security infrastructure must be followed.
Enforced internet connection over company headquarters
In order to sustainably counter attacks from the internet, it can be centrally specified that the selection over a VPN tunnel to the company network and its security infrastructure must be followed.
FIPS Inside
NCP's Secure Clients integrate cryptographic algorithms according to the international FIPS security standard. The embedded cryptographic module, containing the corresponding algorithms, is certified according to FIPS 140-2 (Certificate #1051).
A Remote Access VPN requires Economical Efficiency and Universality:
An investment that pays off
From a commercial point of view, a remote access VPN has to pay off as fast as possible. This means comparing investment costs and operating costs (total cost of ownership) and avoiding hidden costs. In this, savings of up to 85% are possible.
NCP designed its remote access VPN solution with cost savings in mind. Savings are made at client and central-sided components and are based on the following fundamental benefits:
- Standardized software
- "Out of the Box" solution
- Modular software architecture
- Well-matched VPN components
For the high compatibility level of NCP's software, the investor can continue to use already existing IT infrastructure. Additionally he can expand his VPN according to his needs and according to the latest technological standards, because of the availability inexpensive updates and upgrades for all software components. Installation and operation, especially with complex VPN environments, drive up costs. Sometimes rollout costs alone, already exceed investment costs of a VPN solution. In certain industries, like in the insurance industry which is characterized by high staff turnover (25 - 30% p.a.), operation costs are incredibly high. Minimizing these cost drivers is part of NCP's Secure Enterprise Management. As central intelligence of the system it offers all necessary features for fully automatic operation of a VPN.
NCP Remote Access VPN - an overview of the most important features:
- Minimization of support costs/Protection against manipulations
- Minimization of administration costs
- Minimizing costs of identity and access management
- Minimizing communication costs
- Integrated personal firewall with central management
- Central management with integrated unlimited radius server
- Multi company support (VPN Gateway Sharing)
- Bring your own device
- Virtualization
Minimization of support costs/Protection against manipulation
Support costs take up a high relative importance under "Total Cost of Ownership" (TCO). It is worthwhile to keep it as low as possible. For network administration this means a preference for certain client configurations from a central place. Parameter locks hinder subsequent manipulation, whether intentionally or through an accidental operation. Furthermore, the intuitive graphical user interface with error reports in clear text, permits quick fixes for malfunction events.
Minimization of administration costs
The NCP VPN Management serves as a single point of administration for all the efficient operations of a VPN required performance features. For example, it shortens the time exposure for rollout, certificate administration and software distribution. Required changes, e.g. with changes in personnel/staff turnover, they are effectively resolved in real time. This relieves network administration and leads to massive cost savings.
Minimizing costs of identity and access management
NCP's VPN solution is fully compatible to all common network technologies and operating systems. Through this, the software can be easily integrated into existing identity and access management systems (IAM). Time and money consuming upgrades of existing systems and expensive new investments into IT infrastructure become obsolete.
Minimizing communication costs
A Budget-Manager for full cost control is now integrated in the new NCP VPN Client for Windows. The Budget-Manager serves to monitor the costs of all available connection types, focusing on UMTS, GPRS as well as WLAN connections. For this purpose, the administrators or users configure volume or time limits according to the basic provider rates. Should the user exceed his set limit, depending on the settings either a warning notice appears or further connection attempts are hindered. The Budget Manager also allows the restriction or disabling of roaming. Nasty surprises in the provider invoice are avoided in this manner.
Integrated data compression aid further cost savings. This feature is very effective and leads to savings of up to 25% in tariffed transmission networks.
The Short Hold Mode guarantees that no communication costs occur if no user data is sent or received during a session monitored by NCP's software. When the teleworker continues his session, he does not have to login to the central VPN gateway again. He can resume his work from where he stopped his activities. This even works under "difficult" conditions, if for example peripheral Citrix clients are used.
Integrated personal firewall with central management
All NCP VPN Clients are disposed according to standards over an integrated personal firewall. The expense for evaluation, licensing and installation of a supplemental personal firewall is removed. Administration and maintenance can take place optionally from a central place.
Central VPN Management with Integrated unlimited RADIUS Server
ntegrative component of the NCP VPN Management is, next to an integrated control and monitoring mechanism, a RADIUS Server. Already available RADIUS systems can be pooled, and thereby be replaced in an economical manner.
Multi Company Support (VPN Gateway Sharing)
This feature allows for concurrent operation of several VPNs of various companies via a single NCP Secure Enterprise VPN Server. The provider sets up a closed VPN for each company (client) – only the employees of this company have access to this particular VPN. Several independent systems become obsolete through this VPN gateway sharing. Managed Security Service Provider (MSSP) utilize this economic advantage for setup and operation of managed VPNs.
Bring your own Device (BYOD)
In this concept, employees work with their own end devices. BYOD concepts increase user satisfaction and with this productivity. In order to let the company fully profit from these benefits, NCP's remote access VPN solution supports a wide range of operating systems. With this all devices can be integrated into a comprehensive VPN.
Virtualization
Currently, virtualization is the most important IT technology. It contains many measurable benefits for a data center - amongst others: increased efficiency and availability, cost savings and higher productivity. NCP's solution is 100% software-based. It offers all prerequisites for substantial cost savings during installation and operation - even of larger VPN environments.
5 Key Benefits of Remote Access VPN Central Management:
While the purpose that virtual private networks (VPNs) serve is fairly straightforward, the technology components that enable them can be rather complex. Fortunately, central management can go a long way in terms of alleviating concerns around securing remote access by making organizations more secure, efficient and productive.
Here are five major reasons why.
Single Point of Administration
Central management provides a single point of administration so that as companies expand, and the number of users or endpoint devices increases, the network never becomes too complex to operate securely and efficiently. The ability to automatically scale up and down depending on organizational needs is crucial, and central management allows IT administrators to do exactly that by enabling them to:
- Simultaneously manage 100 to 50,000+ connections
- Automate roll-out of company-wide VPN software updates, monitor policy compliance and easily provision or deprovision user access
- Easily scale up or down based on the latest organizational needs
- Integrate with an existing user database (such as Active Directory)
Increased Productivity
Central management has proven critical in optimizing the efficiency of the workforce through the following:
- Freeing up IT staff & administrators from daily mundane tasks, allowing more focus on innovation
- Reducing frequency of user error
- Fast rollout and easy updates
Cost Savings
Central management is an excellent way to reduce the cost of operating a remote access infrastructure. Cost-savings result from automating activities that previously had to be done manually, and often on a user by user basis, and include, but are not limited to:
- Allowing easy client rollout as well as software and certificate updates
- Automating client configurations following user authentication
- Eliminating the need to manually monitor the network for user errors
- Reducing the volume of IT help desk calls
- Doing away with informing individual users of needed updates that need to be manually applied
- Cutting down on the amount of user documentation and training required
BYOD Support
Mobile device manufacturers and service providers are continuously bringing to market new products. Central management can support a wide range of devices and the latest operating systems, as well as previous versions – an ability that can help enterprises without an official bring-your-own-device (BYOD) policy begin to implement one.
Investment Protection
Key to the concept of central management is the ability to integrate within an existing infrastructure so that previous investments in third-party software or hardware are not wasted. This is accomplished through:
- Support for 3rd-party VPN gateways, including, but not limited to, Cisco, Juniper, Check Point, Fortinet and more
- Easily working in unison with other infrastructure elements to build defense in depth network security
- High availability support to provide enough redundancy to keep the network fully operational if failure occurs
Resources:
Download the Enterprise Brochure (PDF).
Download the Benefits of NCP Secure Communications Solutions Brochure (PDF).
Download the NCP Next Generation IPsec VPN Brochure (PDF).
