
NCP Secure Entry mazcOS Client
Simple and Highly Secure Remote Access via Internet
*Price per user. Quantity must be 1 or greater
Get a Quote!
*Price per user. Quantity must be 10 or greater
Get a Quote!
More pricing below, click here!
Overview:
The NCP Secure Entry macOS Client enables easy VPN access with just one click for macOS 10.14 Mojave/10.13 High Sierra/10.12 Sierra or OS X 10.11 El Capitan/10.10 Yosemite. The IPsec standard forms the basis of highly secure data connections to VPN gateways of all well-known providers. The connection is set up via any network (including iPhone tethering via USB or Bluetooth). From anywhere in the world, mobile users can access a corporate network with their Mac. The NCP Secure Entry macOS Client is easy to install and to use. And the intuitive, graphical user interface shows all connection and security states before as well as during data connections.
Features:
Secure
Rely on high-quality IT security software made in Germany
- IPv6 supported dynamic personal firewall
- data encryption
- strong authentication (e.g. biometrics)
- multi-certificate support
- parameter locks
- FIPS Inside
- Apple Keychain Support
Efficient
Mindful of one of the biggest challenges organizations face – cost savings
- compatible to all major VPN gateways
- works in any remote access VPN environment
- import of file formats: *.ini, *.pcf, *.wgx, *.wge and *.spd
Ease of use
Reduced IT complexity
- a single and easy-to-use user interface (one click) for the connection setup
- a reliable, uninterrupted VPN connection
- automatic, location-aware adaption of firewall rules through the NCP VPN Client
- automatic media detection
- seamless Roaming
Mobile
The best mobile device user experience
- Working without dropped connections or interruptions even when switching between networks, i.e. seamless roaming
- auto-connect to your corporate network
- reliable and uninterrupted VPN connections
- Remote Access even behind firewalls, whose port settings typically deny IPsec based communication, i.e. NCP Path Finder® Technology
Technical Data:
| Secure Entry Client for Mac OS: Technical Data | |
|---|---|
| Operating Systems | macOS 10.14, macOS 10.13. High Sierra, macOS 10.12 Sierra, OS X 10.11 El Capitan, OS X 10.10 Yosemite |
| Security Features | The NCP Secure Entry macOS Client supports the Internet Society’s Security Architecture for the Internet Protocol (IPsec) and all the associated RFCs |
| Personal Firewall | Stateful Packet Inspection IP-NAT (Network Address Translation) Friendly Net Detection (Firewall rules adapted automatically if connected network recognized based on its IP subnet address or an NCP FND server) Differentiated filter rules relative to: protocols, ports and addresses, LAN adapter protection In contrast to the application based configuration of the built-in Mac OS X firewall, the configuration of this firewall is port based. The option “Do not allow VPN connection in friendly networks" has been added under “Friendly networks" in the firewall configuration. If this option is activated, the client cannot establish a VPN tunnel when connected to a friendly network. |
| Virtual Private Networking | IPsec (Layer 3 Tunneling) IPsec proposals negotiated via IPsec gateway (IKE Phase 1, IPsec Phase 2) Communication only in tunnel Message Transfer Unit (MTU) size fragmentation and reassembly Dead Peer Detection (DPD) Event log Network Address Translation-Traversal (NAT-T) IPsec Tunnel Mode |
| Key Exchange | IKEv1 (Aggressive Mode und Main Mode): Pre-shared key, RSA, XAUTH; IKEv2: Pre-shared key, RSA, EAP-MS CHAPv2, EAP-MD5, EAP-TLS, EAP-PAP, Signature Authentication (RFC 7427), IKEv2 Fragmentation (RFC 7383) |
| Authentication | User authentication: XAUTH for extended user authentication, One-time passwords and challenge response systems, Authentication details from certificate (prerequisite PKI); Support for certificates in a PKI: Multi Certificate Configurations for PKCS#11 and PKCS#12; Machine Authentication: Authentication with certificates from filesystem or the OS X key ring; Seamless Rekeying (PFS); IEEE 802.1x: EAP-MD5: Extensible Authentication Protocol (Message Digest 5), extended authentication relative to switches and access points (Layer 2); EAP-TLS: Extensible Authentication Protocol (Transport Layer Security), extended authentication relative to switches and access points on the basis of certificates (Layer 2); RSA SecurID Ready |
| Encryption and Encryption Algorithms | Symmetric processes: AES-CBC 128, 192, 256 Bit; AES-CTR 128, 192, 256 Bit; AES-GCM 128, 256 Bit (only IKEv2); Blowfish 128, 448 Bit; Triple-DES 112, 168 Bit Dynamic processes for key exchange: RSA until 4096 Bit; ECDSA until 521 Bit, Seamless Rekeying (PFS); Hash Algorithm: SHA, SHA-256, SHA-384, SHA-512, MD5; Diffie-Hellman-Groups: 1, 2, 5, 14-21, 25-30 (from Group 25: Brainpool curves) |
| FIPS Inside | The IPsec Client incorporates cryptographic algorithms conformant with the FIPS standard. The embedded cryptographic module incorporating these algorithms has been validated as conformant to FIPS 140-2 (certificate #1747). FIPS compatibility is always given if the following algorithms are used for set up and encryption of the IPsec connection:
|
| Public Key Infrastructure (PKI) - Strong Authentication | Biometric Authentication (macOS 10.12 Sierra or higher) X.509 v.3 Standard; PKCS#11 interface for encryption tokens (USB and smartcards); PKCS#12 interface for private keys in soft certificates; PIN policy; administrative specification for PIN entry in any level of complexity; Revocation:
|
| Networking Features | Any type of network, iPhone tethering via USB or Bluetooth |
| Secure Network Interface | Interface Filter
|
| Network Protocol | IP |
| Communications Media | LAN Communications media supported using Apple or 3rd party media interfaces and management tools:
iPhone tethering via USB or Bluetooth |
| VPN Path Finder | Fallback to HTTPS (port 443) from IPsec if neither port 500 nor UDP encapsulation are available (prerequisite: NCP Secure Enterprise Server V 8.0 and later) |
| IP Address Allocation | DHCP (Dynamic Host Configuration Protocol); IKE Config Mode (IKEv1); Config Payload (IKEv2); DNS (Domain Name Service): gateway selection using public IP address allocated by querying DNS server. When using Split-Tunneling, those domains whose DNS packets are to be routed via the VPN Tunnel can be specified exactly |
| Line management | DPD (Dead Peer Detection) with configurable time interval; Timeout; VPN on demand for the automatic construction of the VPN tunnel and the exclusive communication about it |
| Data Compression | IPCOMP (lzs), deflate |
| Additional Features | UDP encapsulation, import of the file formats:*.ini, *.pcf, *.wgx, *.wge and *.spd. |
| Internet Society RFCs and drafts | RFC 4301 (IPsec), RFC 4303 ESP, RFC 3947 (NAT-T negotiations), RFC 3948 (UDP encapsulation), IKEv1, RFC 3526, ISAKMP, RFC 7296 (IKEv2), RFC 4555 (MOBIKE), RFC 5685 (Redirect), RFC 7383 (Fragmentation), RFC 7427, 3279 Section 2.2.3, 3447 Section 8 (Signature Authentication), RFC 5903, 6954, 6989, 4754 (ECC), RFC 2451, 3686 (AES with ESP), 5930 (AES-CTR), 4106 (AESGCM), 5282, 6379 (Suite B), RFC 3447 Section 8 (Padding) |
| Client Monitor | Multilingual (English, German) Monitor & Setup: de, en Online Help and License de, en |
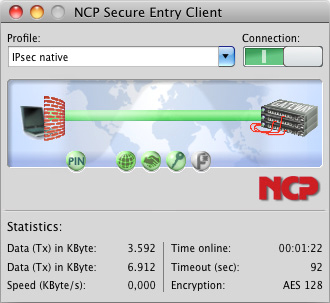
| Intuitive, Graphical User Interface | Traffic light icon indicates connection status Configuration, connection statistics, Log-book (color coded, easy copy&paste function) Password protected configuration and profile management Trace tool for error diagnosis Monitor can be tailored to include company name or support information Options for starting the Monitor automatically after system reboot: either maximized, or as an icon in the menu bar |
| Tip of the Day | The field is integrated into Client Monitor where configuration tips and application examples can be displayed. A mouse click in this field opens an HTML page, that provides information on how to use the Client and other feature. The tips are changed on a day-by-day basis |
| Project Logo | Clicking on the banner in an additional field in the Client Monitor will open a local HTML page in the Mac OS X’s default browser. The banner can be replaced by a company logo and the local HTML page by a page of your choice. Both files are located in the Client’s installation directory under /ProjectLogo as logo_en.png and secure_entry_banner_en.html. In addition a “Quick-Info“ tip can be displayed when the mouse moves over the banner |
Documentation:
Download the NCP Secure Entry Client for Mac OS Datasheet (PDF).
Pricing notes:
- Pricing and product availability subject to change without notice.
- For more than 50 users, please use our Quote Request Form!
*Price per user. Quantity must be 1 or greater
Get a Quote!
*Price per user. Quantity must be 10 or greater
Get a Quote!
*Price per user. Quantity must be 25 or greater
Get a Quote!
*Price per user. Quantity must be 1 or greater
Get a Quote!
*Price per user. Quantity must be 10 or greater
Get a Quote!
